Menu tabs on right to view relevant business/product.
This site:
VicBennett.com
Email:
Vic Bennett
- Custom designs of software and hardware products.
- Architecture development of system level solutions.
- Diagnostic and resolutions of problematic legacy products.
- Responsible for the design of more than a hundred of commercial products comprising
- software (assemblers, compilers, parsers, simulators, OS applications, drivers, control systems, computational algorithms,...)
- hardware (emulators, processors, routers and bridges, high security networks, database hardware, wireless/spread-spectrum products,...);
with patents in most areas.
- Typical languages: C, JavaScript, HTML/CSS, PHP, Python, SQL, assembly, Verilog, VHDL
- Responsible for the founding and technology of companies that have sold for as much as half a billion dollars.

Sites:
gopaq.com
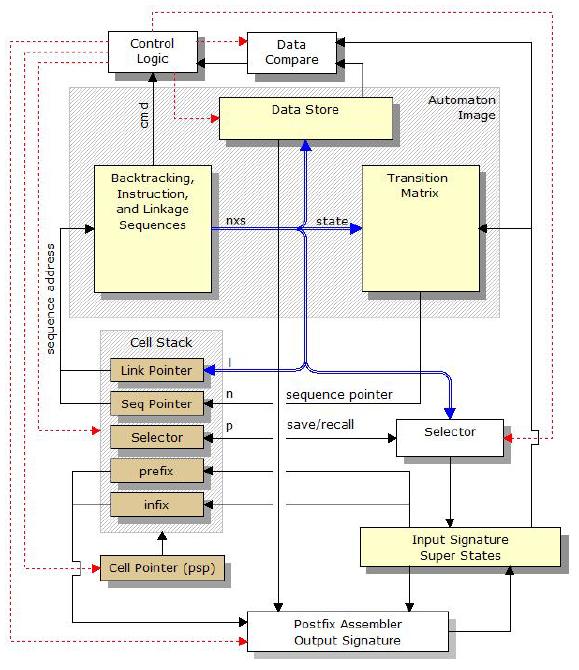
Language processing
-
Adaptive process/language automaton. As part of the compilations, all possible backtracking sequences are pre-computed and merged with application specific operations. Executable as a DLL or for greater performance via a hardware implementation.
-
Search: less than 1 µsec to retrieve a match out of 64 billion. (2 µsec learn time per item)
-
Sorting: linear sort time of up to 64 billion items.
Visral L.P., Co-Founder
Cryptographic Communication:
The Visral Agent stands guard between the Internet and browser. As well as encrypting all communication from end to end (not just to the server), Visral validates the author and recipients that they are who they say they are.
Content is encrypted and secured on the Client’s own machine where it cannot be blocked from the user’s own access. And, no one can access it unless given the right. Visral itself is unable to access any of user’s messages or content.
-
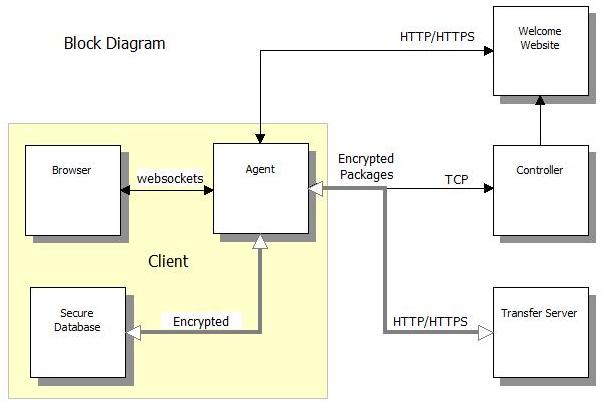 When an Agent connects with a Community it begins by contacting the Welcome website. There it identifies itself and retrieves an IP address, relevant ports numbers, a magic signing expression, and a public RSA signature, all of which are required for connecting to a Controller. It leaves behind its source IP address for further security processing.
When an Agent connects with a Community it begins by contacting the Welcome website. There it identifies itself and retrieves an IP address, relevant ports numbers, a magic signing expression, and a public RSA signature, all of which are required for connecting to a Controller. It leaves behind its source IP address for further security processing.
-
The Agent then connects to the Controller and utilizes a dynamically changing RSA 2048 based protocol to establish its identity and validate the identity of the Controller. (During the Agent registration process, a RSA 4096 signature is used.)
-
The Controller establishes a unique AES 256 encrypted channel with the Agent and provides a URL for the transfer server associated with the selected Community. If this secure channel is in use for an extended amount of time, a process is triggered to re-establish the connection with a new AES key by re-entering step 2.
To log into the agent, enter the password (passphrase) and click LOG IN. The magnifier to the left allow the password to be displayed as it is typed.
With sufficient traffic, meta-data tracking is near impossible due to the lack of correlation between incoming and outgoing messages, sessions lasting less than a second, and arbitrary exchange locations.
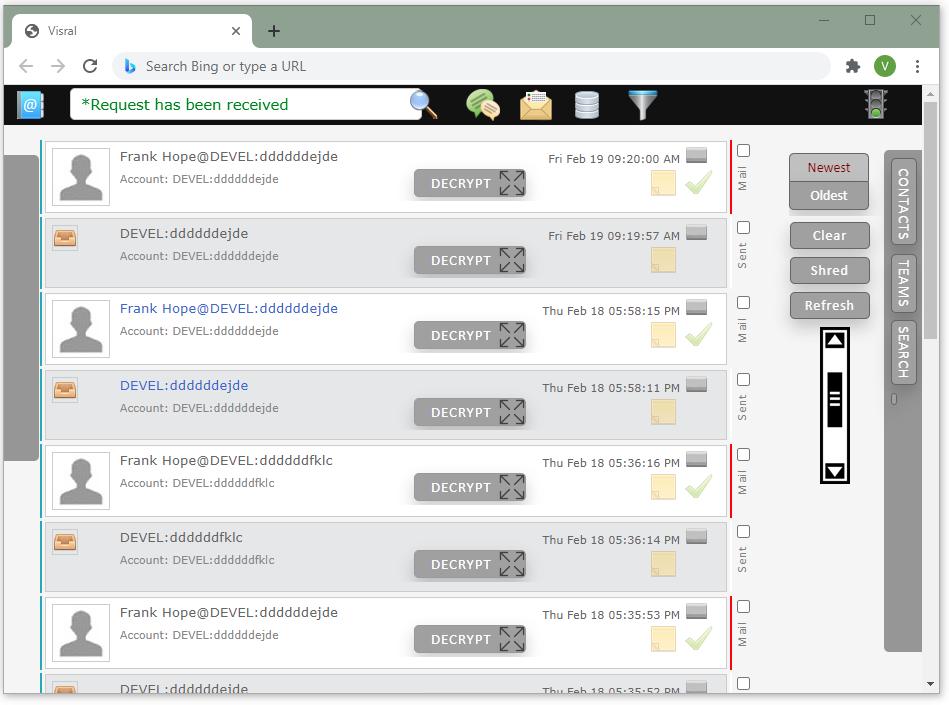
Registering an Account with a Community
-
Super Agent fills out the Create Account menu for the new employee. Pushing the Register button causes an encrypted descriptor to be sent to the appropriate Controller, which in turn adds the employee to its database and issue an invitation email with an Authorization Code.
-
The employee receives invitation email and using Community Authorization Code completes filling in the Join Community menu. The employee’s Agent communicates with the Controller to complete the validation of the account.
SQXL, Founder
Statistical, Scientific, and Business Solutions / Python Operating Environment:
Pertinent Sites:
sqxl.com /
sqxl.net
-
SQXL bridges between Python's powerful financial and scientific solutions and the interactive windows environment users have come to expect.
-
Intuitive enough for everyone to use. Powerful enough for the innovative to rapidly create and deploy custom solutions.
Automaton Builder
| Create/Edit: | Syntax/State/Flow Diagrams Graphically with Drag and Drop.
|
| Convert: | EBNF, ABNF, XBNF, and XML EBNF to Syntax Diagrams.
|
| Generate: | Parsers & State Machines directly from Syntax Diagrams.
|
| Convert: | Syntax Diagrams to EBNF.
|
| Detect: | Direct and Indirect Recursive Terms.
|
| Automated: | Removal of Direct Recursive Terms.
|
| Automated: | Simulation and Trace to validate Grammar & State Rules. |
| Supplied: | DLL Source Code for rapid implementation. |
| Supports: | Virtually unlimited number of instances of Parsers and SMs. |
| More: | Generate Intermediate Postfix Representation
Automated Common Term and Rule Reduction
Automated Real-time Placement and Routing of Diagrams
Streaming LL(1) Parser with capacity to stop and restart
Portray Precedence within Syntax Diagrams
Print or Paste Syntax Diagrams into other documents
|


EBNF Forms
Utilizing the output of the Automaton Builder (SQXL) is composed of two arrays that configure the language processor. It is capable of implementing complex handshaking and dynamic data processing. The processor can be implemented via software or hardware. A DLL is available simplifying the software approach and schematics for the hardware.
When employing SQXL's learning elements, it is capable implementing adaptive modelling (trueAI).
Language processing model
-
Adaptive process/language automaton. As part of the compilations, all possible backtracking sequences are pre-computed and merged with application specific operations. Executable as a DLL or for greater performance via a hardware implementation.
-
Search: less than 1 µsec to retrieve a match out of 64 billion. (2 µsec learn time per item)
-
Sorting: linear sort time of up to 64 billion items.
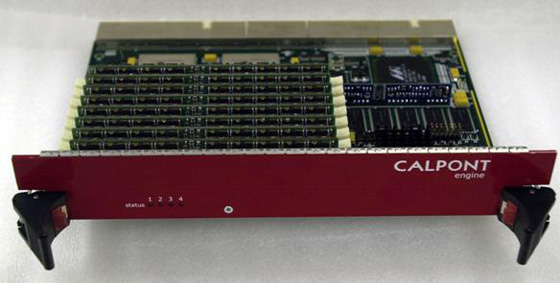
Calpont, Inc., Co-founder and Investor
Hardware Database Products:
-
Calpont's Database Platform was specifically designed to meet the high performance
needs of large distributed access database applications.
Calpont's technical foundation was in part based on algorithms that enable the efficient insertion
and selection of very large amounts of weakly correlated data in compact arrays of memory. The resulting
performance necessitated the creation of other speed matching components leading to such solutions as the
hardware SQL engine.
-
Calpont SQL Manual
More
Technical Guide
More
Installation Guide
More
-
Calpont database performance brief
More
-
Calpont Hardware Engine Card
Agere, Inc., Stockholder, Board member and Consultant
Network Processors:
-
Agere was formed in 1997 with an 8 million dollar investment and a limited license to the
ETAC patent. More
Agere’s product line was based on an updated version of the original ETAC
algorithms.
Ten months later a second
round was contemplated with the inside investors offering a 75 million dollar valuation.
With an agreement to sell the remainder of the license to Agere for 2 million dollars, the inside investors
agreed to raise their valuation to 150 million.
By that time, 65 million in unsolicited investment
offers were received and bids from two companies for approximately half a billion each.
Fourteen months from its founding Agere was sold to Lucent for 440 million dollars. It was later understood
that 1 billion had been set aside by one of the bidders for the purchase of Agere.
Original product proposal.
More
Agere press release.
More
-
Netrake Corp., Co-founder and investor - Netrake was formed and funded at about the time Agere was sold. It utilized the Agere
chip set as well as another set of memory performance algorithms to address
recognition of the contents of high-speed network traffic.
Netrake's customers including NTT, SBC, and Level3, were attracted by its ability to provide network integrity and
service differentiation through content awareness.
Acceletek, Inc., founder
Consulting and Licensing of communications and other products:
-
Update design of 960 based Access Device and Concentrator to use EDO memory. [NetLink’s NetFRAD(AT&T FrameRelay Choice) and OmniFRAD series of products]
More
More
-
PCI based Modular multi-processor Engine (Used Altera 8452 and two 8820.) with 1.6 Gbps (64 bit main memory) of bandwidth for video server and comm applications with a PCI Master/Slave Interface constructed in single Xilinx 4006E; including Channel Connect and Ethernet daughter cards. [Connectware, Inc.]
-
Feed-forward and Adaptive Control System for Varian Ion Implanters (written in C) providing a 300 percent improvement over PID control . -- Required by INTEL in the manufacture of the Pentium Chip. [Varian Extrion] More
-
ATM Switching Technology; Entropy Switching. [Developed at the request of HP.] -- Performance verified at the HP Bristol Labs.
-
960 based Bridge/Router and WAN Server [IDEA Associates’ RIAC board] with 2-8 Meg DRAM, Interleaved SRAM, CAM, FLASH, EEPROM, SCA, ISA... supporting “SNA, TCP/IP, Novell SPX/IPX, SNMP(MIB II), and RIP” with Ethernet, “Token Ring, and WAN HDLC/LAPB” with (RS232, X.21, V.35) interfaces.
More
-
960 based Integrated Access Device [BBN’s T10, Contracted April 24, delivered working prototypes which were shipped straight to end users mid August] with Dual 2-8 Meg DRAM Memories with Parity, up to 12 SCAs (24 ports), 4 Meg FLASH, EPROM, Serial Port, ISA... supporting “CCITT X.3/X.28/X.29 Async, 3270/2780/3780 Bisync, SNA/SDLC, TCP/IP(including ARP, BGP, EGP, ICMP, SNMP, SPF, Telnet, and TFTP), and Ethernet”, RS232, V.35, X.21 interfaces.
More
-
960 based Access Device and Concentrator [Amnet’s RSIC product line and NetLink’s OmniLinx series of products] with Single or Dual 960, 2-8 Meg Interleaved DRAM, 256K SRAM, up to 4 SCAs (8 ports), EEPROM, 640 Megabit Inter-board Packet Bus, ISA... supporting “Frame Relay, SNA/SDLC, Async, Bisync, X.25”, with RS232/V.24, RS530, RS449, X.21, V.35, “T1/E1-DS1”) interfaces.
More
More
-
Monitor and Development System for Communication Controllers; written in 960 assembly and C. -- Used for the development of the above products.
-
960 Accelerator, plug compatible with the 960 providing Transparent Double-Buffering and DMAing. Increased host ethernet speed 50%. [Coral Networks, Inc.]
-
State Machine Compiler written in Prolog. Used in the design of other products.
-
Blood Gas Analyzer Process and Control System with software written in for 68HC11 in C.
-
VGA Enhanced Color Development System written in C.
-
Provided a custom high performance Acoustic Processing DSP Memory System design for speciality company in Cambridge Mass.
Obtek, Inc., founder
Consulting and Licensing of communications and other products:
-
Coral Acquisition, Corp., Shareholder, Consultant - Communication Products:
ETAC based 32 Port High Performance FPGA Implemented Communication Controller capable of bridging and routing a million packets per second, supporting FDDI, Ethernet, Token ring, T1, etc. -- SynOptics purchased company to acquire the limited license to ETAC. Synoptics then merged with Wellfleet to become Bay Networks, which in turn was acquired by Nortel.
-
Developed new algorithms that reduced ETAC memory requirements by 60% and increased performance by 250%.
-
Two days following the purchase of Coral, HP call and asked for a presentation. The HP PA RISC group signed NDA and received a presentation of Obtek's technology. Over a number of months HP evaluated the incorporation of ETAC, but concluded the architecture differences would require many significant changes to their finely tuned designs.
-
Transferred rights to SynOptics at time of their purchase of Coral. The merger of SynOptics and Wellfleet to Bay Networks, permits Bay to use the license. The chairman of the board, Paul Severino, has announced to stock analysts that they will be using the technology in their next generation of products.
-
Sold limited non-exclusive license to Coral Acquisition Corp for use in bridging, routing, and switching equipment that primarily perform bridging, routing, or switching and are not end station. Can not be implemented as a standalone chip and must work as a slave.
-
Sold ETAC Evaluation Kits to AT&T, Nortel, Siemens, and others.
-
Developed a programming language to allow intuitive and rapid descriptions and parsing of protocols. Used with the ETAC Evaluation Kits and later in the Agere product development.
-
Developed ETAC (Executable Translation Array Coprocessor) and filed for patents. The patented algorithms that allowed the way data was stored in memory to significantly increase computational performance.
More
-
Coral Network, Corp., Co-founder, Consultant - Communication Products:
32 Port, 800 Megabit High Performance Discrete(FPGAs + PALs) Communication Bridge capable of 375,000 packets per second filtering and forwarding supporting FDDI, Ethernet, Token ring, T1, T3 and more.
More
Cygic, Inc., founder
Joint venture with Intelligent System:
-
20 MHz 80386 PC/XT converter/accelerator with 1 Meg of memory and BIOS. - “BIOS done by others” [QuadRam’s Quad386XT]
More
-
20 MHz 80386 MS/DOS-compatible Single Board Computer with screen and disk accelerators - “80% of BIOS done by others”
-
Tempest PC to 386 Adapter Card for Argonne National Labs
-
10 Mips 8086 MS/DOS-compatible processor with BIOS (600 ic’s) — 25 Mips @ 33 Mhz in 1 micron silicon.
More
More
More
-
10 MHz 8086 PC/XT async accelerator with 32K/92K cache/image of DRAM, and async write-back.
-
10 MHz 8086 MS/DOS-compatible Single Board Computer with hardware screen and disk accelerators - “80% of BIOS done by others”
More
-
AT BIOS parsing for transparent cascaded multiprocessor operation.
-
XT and AT BIOS upgrades, and EMS and device drivers [written in x86 assembly]
-
PC/XT and AT EMS memory boards, and AT Multifunction/EMS boards [QuadRam’s Liberty-PC, Liberty-AT, and Quadboard-AT]
More
-
The first EMS board and device driver to be demonstrated at Comdex; before Intel and Lotus, the authors of the specification could get a product produced.
-
Keysaver software Video/Multifunction board. [QuadRam’s Gold-Quadboard]
-
9.54 MHz 8086 PC/XT synchronous accelerator with 4K static cache. [QuadRam’s QuadSprint]
More
Emulogic, Inc., Co-founder, VP of R&D
Development System Products:
-
PDP11 based Universal Development System.
-
Interface Pods for 8086/88, 68000/10, 8085, Z80/NSC800, 8048, - (Z8001/2, 8080, 6809, 68C05E3/2, 6502 and its mutants, 8031, 68008, 68200, 80186/188, 9989, 8021 were completed by others).
More
More
More
-
Table driven Universal Cross-assembler in PDP11 assembly.
-
Table driven Universal Cross-assembler Characteristic Tables for 8086/88/186/188, 8085, 8080, 8048/21, Z80/NSC800, 1802, 8X300, - (68000/10/8, Z8001/2, 6809, 6805, 8031/51, 68200, 9989, 6502 were completed by others).
-
Emulator monitor code for the following in their assembly: 8086/88/186/188, 8085, 8080, 8048/21, Z80/NSC800, 1802, 8X300, - (68000/10/8, Z8001/2, 6809, 6805, 8031/51, 68200, 9989, 6502 were completed by others).
-
Supplied custom emulator based on the MOS Technology 6507 processor to Atari game development.
Security Research Labs, Inc., Co-founder, Director of R&D
Engineering Services:
-
Ethernet to MultiBus II Controller Card. (Bus-Tek).
-
Single-board 8-loop PID controller with time and voltage proportional control, alarm, anti-windup, and non-volatile backup. (Gloucester Engineering).
-
Spread-spectrum, secure communication system for industrial process control.
More
-
Continuous Coefficient-of-Variation specialised computer for real time textile fibre quality monitoring system.
-
Network and Circuit Design Program in C and Basic. -- Used to evaluate and automatically design RF Networks to match desired characteristics.
More
-
Spread Spectrum Processor utilizing a code controlled varactor circuit in place of a xtal clock for the acquisition, modulation and demodulation of spread spectrum signals
-
Patents in spread-spectrum.
-
Imaging system and digital scanner for microfiche-to-COM recorder system
-
Keyboard processing subsystems for fast-food order entry. (Burger King)
-
Military fire control station.
-
Remote data entry and communication for oil fields.
-
Portable intrusion detection and alarm system for retail sales.
-
First low-power radio household warning and alarm system sold commercially.
Currier Smith, Inc., Stockholder, Director of Engineering
Security Products:
-
First digital dialer system on the market. Units installed in every MacDonald’s and Burger King in US. Resold under ADT name.
-
First cryptographic security system US Army was unable to defeat. Sold to major banks, gold refineries, and diamond houses.
-
Infrared disturbance detection system.
-
Various patents.
Northeastern University: Electrical Engineering, Student
-
Developed the algorithms for high speed computing of logarithmic and transcendental functions
while working part time for Mathatronics. Provided the company with a major advantage over its competition.
Became a standard in calculators providing those functions and in certain DSP applications.
Information closest to the particular algorithms can be found under the name, Cordic algorithms.
Notes:
-
The design activities of all listed products include the complete architecture, electrical engineering, programming, and debugging unless otherwise indicated. The ETAC Evaluation Kits and Acceletek listed comm products also included board layout and fab of prototypes quantities.
-
Clicking a green More will reveal supporting documentation below.
-
Acceletek, Obtek, and Cygic were concurrently active.
-
Display pseudo-chronological, newest to oldest: Left to right and top to bottom.
-
Entries in light grey indicate the described products were never commercialized.
![]()


 Content is encrypted and secured on the Client’s own machine where it cannot be blocked from the user’s own access. And, no one can access it unless given the right. Visral itself is unable to access any of user’s messages or content.
Content is encrypted and secured on the Client’s own machine where it cannot be blocked from the user’s own access. And, no one can access it unless given the right. Visral itself is unable to access any of user’s messages or content.
 Registering an Account with a Community
Registering an Account with a Community
 Content is encrypted and secured on the Client’s own machine where it cannot be blocked from the user’s own access. And, no one can access it unless given the right. Visral itself is unable to access any of user’s messages or content.
Content is encrypted and secured on the Client’s own machine where it cannot be blocked from the user’s own access. And, no one can access it unless given the right. Visral itself is unable to access any of user’s messages or content.
 When an Agent connects with a Community it begins by contacting the Welcome website. There it identifies itself and retrieves an IP address, relevant ports numbers, a magic signing expression, and a public RSA signature, all of which are required for connecting to a Controller. It leaves behind its source IP address for further security processing.
When an Agent connects with a Community it begins by contacting the Welcome website. There it identifies itself and retrieves an IP address, relevant ports numbers, a magic signing expression, and a public RSA signature, all of which are required for connecting to a Controller. It leaves behind its source IP address for further security processing.
 Registering an Account with a Community
Registering an Account with a Community




